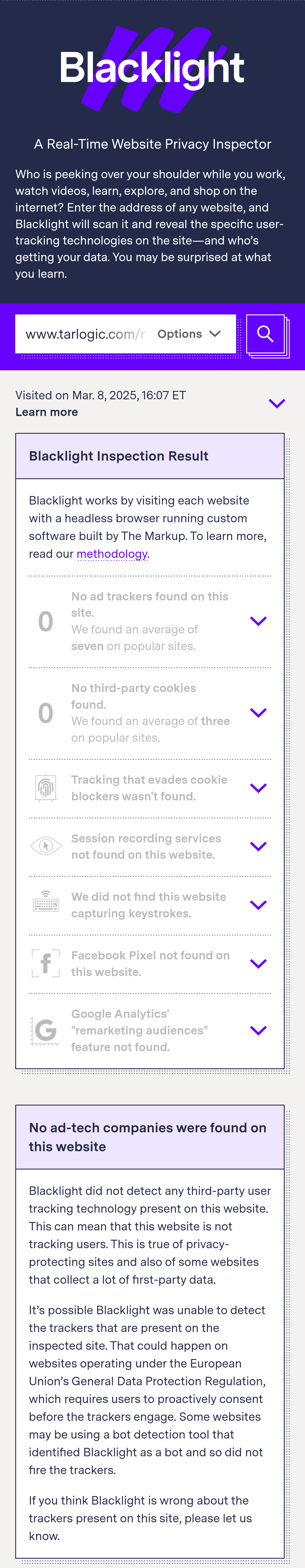
Source Link Privacy.
Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Update: The ESP32 “backdoor” that wasn’t.


There is nothing to “fix”. Undocumented instructions have just been found in the silicon but they are not executable unless the ESP32’s firmware their owner flashed to give it a purpose uses them. No pre-2025 firmware that we know of uses these instructions, and they might turn out to be buggy so compilers might not adopt them. If they turn out OK, the documentation of the instruction set will need an update, and compilers will be able to take advantage of the new instructions.