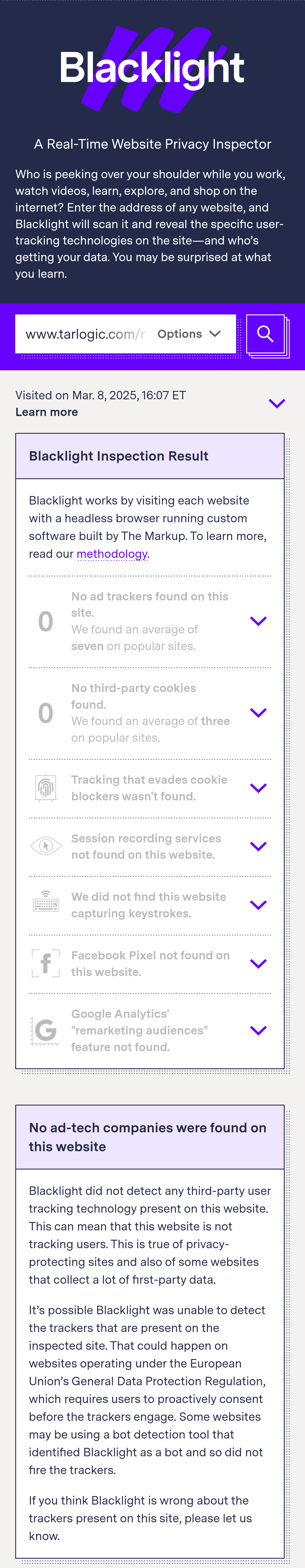
Source Link Privacy.
Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Update: The ESP32 “backdoor” that wasn’t.


Not sure if joking or naive…
Like I said 6 hours ago, just because I can’t mitigate all of the risk doesn’t mean that I shouldn’t mitigate as much as I reasonably can.
My 3d printer is a fire hazard, but that’s no excuse for leaving a bunch of candles unattended.
Ah I missed the other comment, my client still had a cached view apparently. And definitely true regarding mitigation, your phrasing just read funny to me :)